We are reachable through many channels.
- Home
- /
- Contact Us
- /
- Guidance & Awareness
Guidance & Awareness
General Guidance
Cyber security is becoming a hot topic for everybody – the attacks are getting more and more sophisticated, and people that are not experts in cyber security struggle to make their systems secure. The Baseline Security Controls have been developed to list and explain security controls that everybody can and should implement to protect their systems.
The Baseline Security Controls cover all cyber security aspects that a normal person in their day-to-day life might encounter, and their complete implementation is highly recommended to avoid cyber security incidents.
Access Control
Computers, laptops, phones, etc. that are given to you by the organization you are working for should not be used by any other family member or by friends. If there is shared computer use, different user profiles should be established. If children are using a computer, laptop or tablet, child protection should be enabled. Computers, laptops and tablets should use a screen saver that logs out automatically after a defined peri- od of time, e.g. 10 minutes.
Social Media Use
Select strong passwords for social media accounts, a different one for each of them. Close any un-used accounts you may still have. Use a unique email for each social media account. Be aware that all information you are providing on social media might be seen by a far larger group of people than you think.
Awareness
Everybody using computers, laptops or tablets should be aware of the need to operate securely; new trends or attacks should be taken into account.
Back-Up
Back-ups should be made regularly, at least once a week, on media which are stored separately from the computer or laptop used. Back-up software can be used to ease the process.
Security Functions
State-of-the-art firewalls and malware protection should be used; these should always be up to date. Any security patches and updates from trustworthy sources (e.g. Microsoft, Acrobat, etc.) should be installed whenever prompted. Mobile apps should be updated, the latest version should be used.
Email & Internet
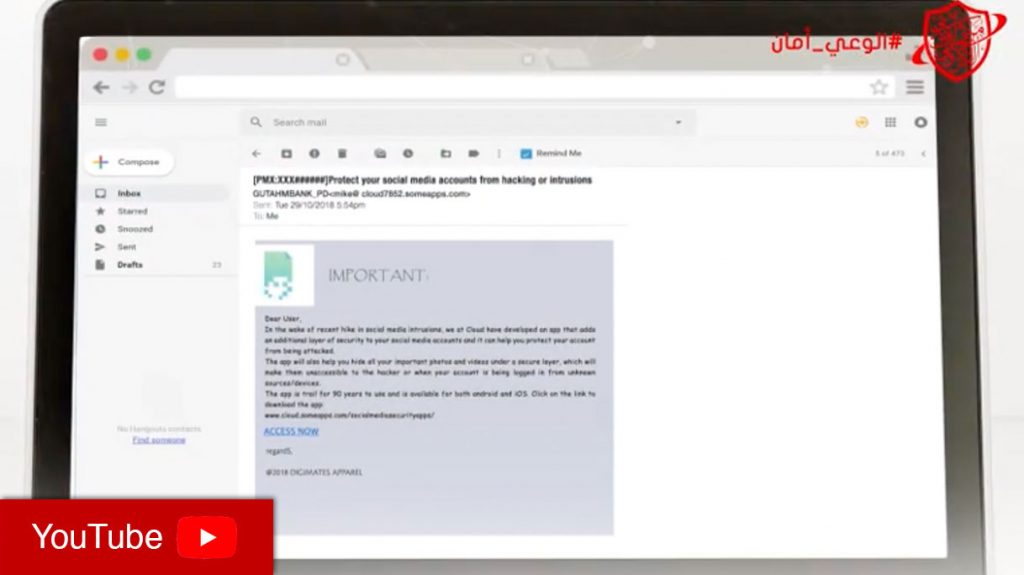
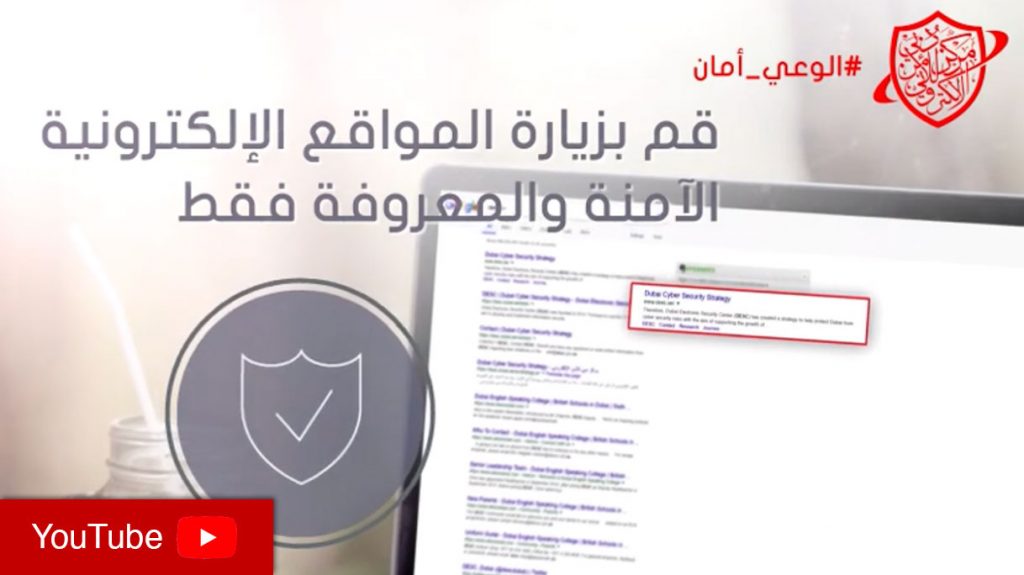
Each person using email should have a separate email account. When receiving emails, the authenticity of an email should be checked before clicking on it. In addition, due care should be taken when clicking on links in emails or opening attachments. Never provide any identification/authentication data to anybody – banks and other serious organizations will never ask for your password, this might be a phishing attack. Be aware that unprotected emails can be easily hacked; normal email should not be used to send sensitive or confidential information. It is advisable to use a spam filter.
Information Sharing
Any USB sticks, flash drives, downloads etc. should only be taken from well-trusted sources (more about that also in the Email & Internet section). Copying important or confidential information on USB sticks or flash drives should be avoided.
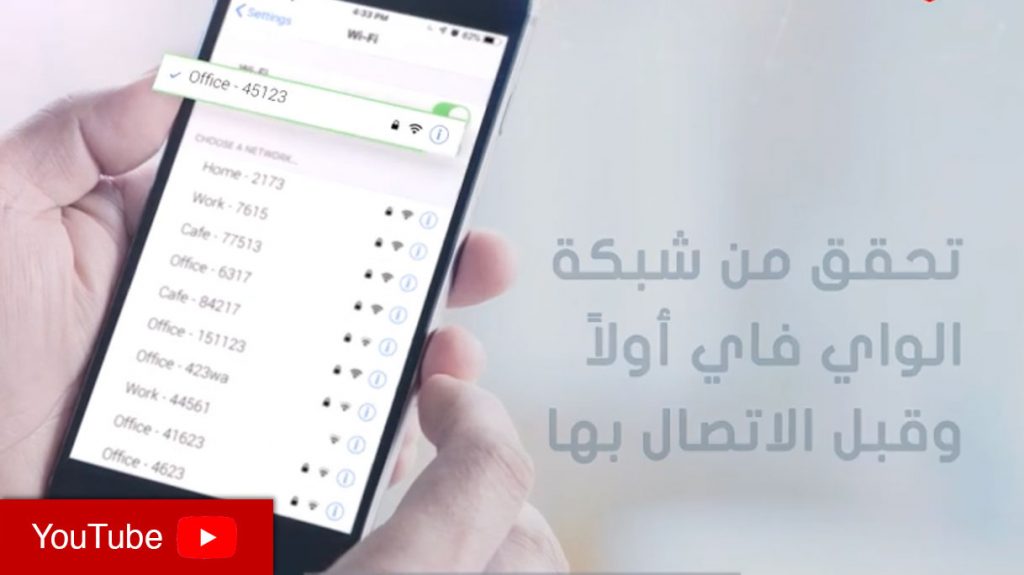
Wireless Networks
Any wireless network used should be protected by a strong password. There should be a separation between guest networks (with an easier password to enable guests to log in) and the wireless network used for normal use. WPA2 should be used.
Identification & Authentication
If possible, biometric user authentication (e.g. a fingerprint) should be used to log into your account. If biometric authentication is not possible, a strong user password should be chosen. Strong passwords are at least 8 characters long and contain at least upper- and lower-case letters, numbers and special characters. Normal words, names, birthdays, etc. should be avoided. Passwords should never be written down or shared, and frequently changed; a password manager can help. If web sites offer two-factor authentication, this offer should be used. Never use the same password for different accounts.