DESC provides a framework for managing cyber risks and supporting government entities.
- Home
- /
- Regulations
- /
- Licenses
Licenses
DESC has developed and introduced a new batch of trade license activities for companies offering cybersecurity related services to other organizations, in collaboration with the Dubai Department of Economic Development (DED).
Further information regarding the DESC license for cybersecurity services can be found on the DED website: www.ded.ae.
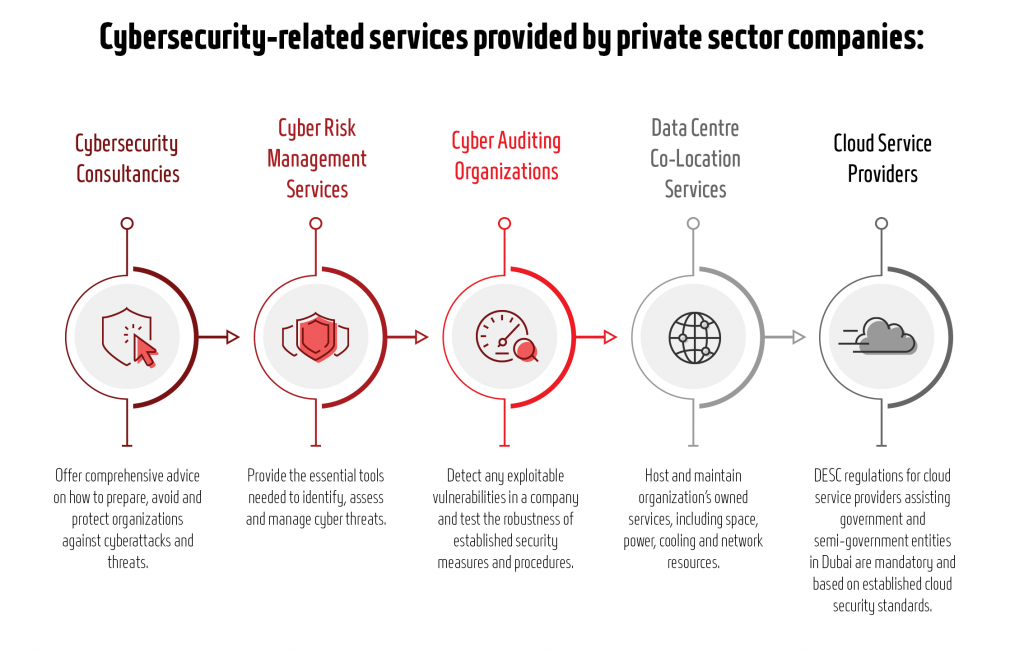
Cyber Security Consultancy
Includes firms specialized in offering comprehensive professional cyber security consultancy to other organizations on how to prepare for, avoid and protect themselves against cyber-attacks and threats, such threats might involve networks, computers, programs and data damage or unauthorized access.
Jamming Equipment Trading
Includes reselling jamming equipment that interferes with wireless communications, such as cordless telephones and GSM repeaters.
Jamming Software Trading
Includes reselling the set of application software for jamming or interfering with wireless communications such as cell phone calls, cordless telephones and GSM repeaters, text messages, GPS systems and Wi-Fi networks.
Encryption Equipment Trading
Equipment for encryption solutions that protect sensitive data across enterprise applications data processing IT, critical transactions, storage and big data platforms.
Encryption Software Trading
Software for encryption solutions that protect sensitive data across enterprise applications data processing IT, critical transactions, storage and big data platforms.
Cloud Service & Data Centers Providers
Includes companies that offer elements of cloud computing, such as software or platform as services provided in the cloud.
Cyber Risk Management Services
Includes firms which help others with the essential tools needed to identify and assess cyber threats which might include users themselves, networks, devices, all software, processes, information in storage, applications, including recommending effective measures to eliminate or manage cyber threats.
Cyber Security Architecture
Includes designing the organization’s specific protective objectives that address the necessities and potential risks involved in the or damage to the hardware, software or the information on them.
Auditing, Reviewing & Testing Cyber Risks
Includes firms engaged in auditing the organizations’ compliance with the standards and documented procedures that identify risks and vulnerabilities within the existing IT environment, also, conducting penetration testing to the established security measure for possible breaches and the exploitable vulnerabilities that an attacker might gain unauthorized access.
Data Center Co-Location Services
Includes firms hosting and maintaining an organization’s owned servers, including space, power, cooling and network resources.
Network Consultancies
Includes providing comprehensive professional consultancies to IT organizations to help them match their needs with the networking solutions, it involves securing, analyzing and designing network solutions that maintain the security and integrity of their IT assets, the minimal qualifications required is bachelor degree in computer sciences or information technology, along with three years hands-on experience.
Information Technology Consultants
Includes providing technical services and consultancies with respect to information technology and applications like internet, internet and data warehousing to enhance the administrative and technical performance in different corporations. In addition to offering consultancies, to involve proposing the adequate software and handling the surveys and studies to determine the appropriate technology consistent with the nature of the firm, these firms are not entitled to market or produce any of the software or products related to said technology, the minimal degree required is BSc in computer sciences or information technology, along with three years hands-on experience.
IT Infrastructure
Includes firms specialized in laying the technical foundations of the information technology, which comprises the network, the systems and the data bases. It also involves firms engaged in preparing the consultative studies along with the installations of the network and the systems.
Public Networking Services
Includes firms specialized in providing the services of subscribing and connecting to international information networking, as well as specialized information banks and exchange of electronic mail. Which includes operating systems and applications such as electronic mail and the exchange of data electronically by using communication networks as well as their local and international lines. The role of those is limited to facilitating subscription procedures against fees or specified amount.